Tag: Apple
macOS vuln in IOHIDFamily
Siguza, 01. Dec 2017 (published 31. Dec 2017)
IOHIDeous
“IOHIDFamily once again.”
This is the tale of a macOS-only vulnerability in IOHIDFamily that yields kernel r/w and can be exploited by any unprivileged user. IOHIDFamily has been notorious in the past for the many race conditions it contained, which ultimately lead to large parts of it being rewritten to make use of command gates, as well as large parts being locked down by means of entitlements. I was originally looking through its source in the hope of finding a low-hanging fruit that would let me compromise an iOS kernel, but what I didn’t know it then is that some parts of IOHIDFamily exist only on macOS – specifically IOHIDSystem, which contains the vulnerability discussed herein.[…]
https://siguza.github.io/IOHIDeous/
https://github.com/Siguza/IOHIDeous/blob/master/docs/index.md
https://github.com/Siguza/iokit-utils
https://github.com/Siguza/hsp4
https://github.com/Siguza/ios-kern-utils
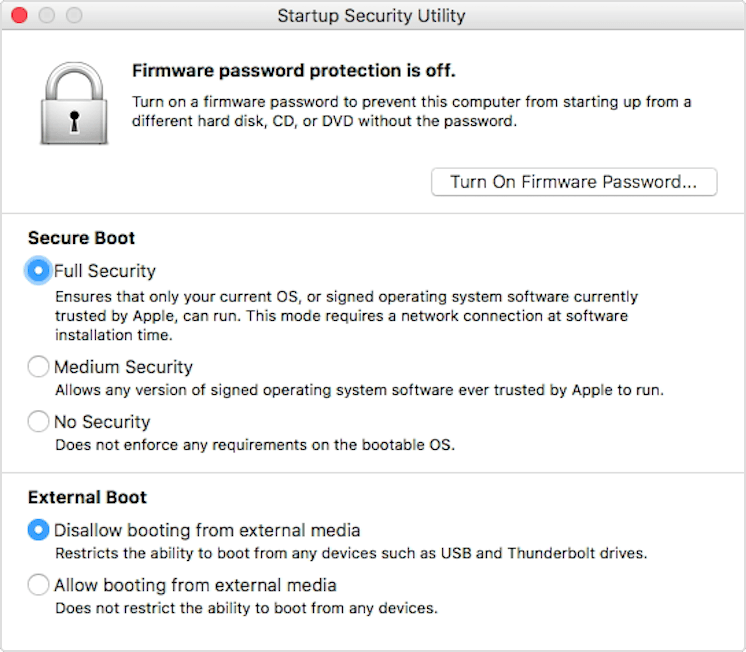
Apple KB article on Secure Boot
Apple has a support article about their new Secure Boot. Interesting to see how Windows works with it, under Boot Camp. I wish Apple would also support Linux with Bootcamp, not just Windows.
https://support.apple.com/en-us/HT208330
Pepijn on Apple use of Intel ME
Interesting, Pepijn Bruienne is looking at new Apple firmware, and how it uses Intel ME.
Apple releases iMac Pro, with firmware security updates
Re: https://firmwaresecurity.com/2017/12/13/apple-secure-boot/
A New Level of Integration and Security
iMac Pro brings a new level of integration and security to the Mac with the T2 chip, Apple’s second generation custom Mac silicon. By designing and integrating several new controllers — such as the System Management Controller, image signal processor, audio controller and SSD controller — T2 delivers new capabilities to the Mac like enhanced imaging processing for the FaceTime HD camera. T2 also enables a new level of security by including a secure enclave coprocessor that provides the foundation for new encrypted storage and secure boot capabilities. Dedicated AES hardware encrypts data on the SSD without affecting performance, while secure boot ensures that only trusted software loads at startup.
https://www.apple.com/newsroom/2017/12/imac-pro-the-most-powerful-mac-ever-available-today/
I wish there was some firmware information in the tech specs:
https://www.apple.com/imac-pro/specs/
Apple seeks UEFI firmware engineer
Mac Firmware Engineer
The Mac Platform Software team is looking for a firmware engineer to join a new Austin-based team responsible for developing Apple’s UEFI implementation and related technologies for the Mac product line. Mac Platform Software is responsible for bringing up macOS and Windows on all new Mac products, including the development and integration of firmware and systems software for macOS and Windows, the development of platform-level features for the Mac, and the leadership of cross-functional debug and optimization efforts across hardware and software teams. A Mac Firmware Engineer is responsible for the development of Apple’s UEFI implementation and its related technologies. UEFI provides the boot firmware for all Mac systems and plays a critical role in system stability, performance, and battery life. This role also contributes to development of the boot loader and firmware update mechanisms, as well as other related technologies. Primary job responsibilities include firmware feature development supporting new Mac software and hardware features, supporting ongoing efforts to improve the quality of shipped Macs in the field, and assisting the larger Mac Platform organization in cross-functional efforts to design and build new Mac products.
* Experience in firmware/BIOS development
* Experience with boot loaders and firmware/kernel interfaces
* Knowledge of UEFI and the x86 platform and standards, including ACPI, SMM, PnP, PCIe, and JEDEC DDR a plus
* Strong understanding of system power management a plus
https://jobs.apple.com/search?job=56183392&openJobId=56183392#&openJobId=56183392
Rafal Wojtczuk joins Apple!
Wow, the Apple firmware team keeps getting more and more amazing talent.
Some older reading on Rafal:
https://invisiblethingslab.com/itl/About.html
http://theinvisiblethings.blogspot.com/2008/07/rafal-wojtczuk-joins-invisible-things.html
https://blogs.bromium.com/author/rafalwojtczuk/
Apple Secure Boot
Apple Insider has a story on new Apple security processor. Caber Sasser reviews a loaner iMac Pro.

FAT-EFI: FAT EFI loader plugin for Hopper Disassembler
This project is a FAT EFI loader plugin for Hopper Disassembler. Apple uses an extension to the standard PE format for EFI binaries to allow FAT EFI binaries that contain both 32 and 64 bits executables. It is very similar to the FAT format, except for a different magic number and for little endianness. This plugin allows to read these FAT EFI binaries with Hopper Disassembler.[…]
https://github.com/pascalwerz/FAT-EFI
Similar: https://github.com/0xc010d/EFIFatBinary.hopperLoader
efivalidate (and mojo_thor)
Rick Mark has released efivalidate, a macOS-centric Ruby-based EFI checking tool. Also, by same author, Mojo_Thor project has activity. I thought it was a one-time drop, but it is actively being updated:
efivalidate is a ruby utility to take a given input EFI payload from macOS and to compare it against Apple’s validation schema. Being written in ruby this can occur off-box to ensure that the utility itself hasn’t been compromised
https://github.com/rickmark/efivalidate
Loki / Thor / Mojo are a triad of Apple internal tools and malware that infects the SMC, EFI and macOS of Apple MacBooks. It is believed that direct access to the hardware is gained by re-flashing the Thunderbolt controller (via ThorUtil)
Apple macOS High Sierra: can login as root with empty password!
Apple SEP story from August, again
[AFAICT nothing new recently, this is just the August story being rehashed again in November, I think…]
Re: https://firmwaresecurity.com/2017/08/17/apple-secure-enclave-processor-sep-firmware-hacked/
https://twitter.com/kwestin/status/934677472293072896
https://www.theiphonewiki.com/wiki/Greensburg_14G60_%28iPhone6,1%29
https://github.com/xerub/img4lib
Arg, WordPress inserts the entire contents of Github Gists into posts. To view sepsplit.c, remove the 2 spaces from below URL, or click on 2nd t.co-based URL in above @xerub tweet.
https://gist. github.com /xerub/0161aacd7258d31c6a27584f90fa2e8c
Click to access us-16-Mandt-Demystifying-The-Secure-Enclave-Processor.pdf
Hackaday:
Duo Labs releases EFIgy 10.13
Trammell: eficheck finds Thunderstrike 2
Trammell Hudson tests Apple macOS’s eficheck against Thunderstrike2:
https://twitter.com/qrs/status/927565241449410560
https://twitter.com/qrs/status/927599689515626496
https://trmm.net/Thunderstrike
https://trmm.net/Thunderstrike_2
https://support.apple.com/en-us/HT207475

Apple EFI malware triad: Mojo/Thor/Loki?
https://twitter.com/osxreverser/status/916404934462939136
https://twitter.com/osxreverser/status/916405321056309249
https://twitter.com/osxreverser/status/916405109617319936
https://twitter.com/osxreverser/status/916473582720638982
Mojo / Thor / Loki are a triad of malware that infects the EFI of Apple MacBooks.[…]
more from Duo on Apple EFI security
Nice, in addition to an upcoming new EFI tool, it appears Duo has some defensive advise, using OSQuery, Puppet, and Chef. Click on the first tweet below for an image from their upcoming presentation.
Note that Teddy Reed is giving a presentation on OSQuery in November at Usenix LISA:
Pepjin’s Apple EFI version spreadsheet:
https://docs.google.com/spreadsheets/d/1qGRVF1aRokQgm_LuTsFUN2Knrh0Sd3Gp0ziC_VIWqoM/edit#gid=0
Nikolaj moves to US
Apple firmware security researcher Nikolaj Schlej has been working from Europe, and is now moving to the US.
Nice picture of the Xeno, Corey, and Nikolaj in the above tweet.
Apple open sources XNU?
https://github.com/apple/darwin-xnu
https://github.com/apple/darwin-xnu/tree/master/pexpert
Does this new Github release contain more than the previous Apple-hosted releases? I’m not yet clear.
Apple macOS automatic EFI checks
https://twitter.com/osxreverser/status/912014988608491520
High Sierra automatically checks EFI firmware each week
Upgrading to High Sierra brings a new and significant security feature: your Mac will automatically check its EFI firmware. In a series of tweets, Xeno Kovah, one of the three engineers responsible for the new tool, has outlined how this works.[…]
AFAICT, the article references Tweets from earlier today that appear to have subsequently been deleted from Twitter.

You must be logged in to post a comment.