Click to access Managed-Runtime-Speculative-Execution-Side-Channel-Mitigations.pdf
Click to access 337879-analyzing-potential-bounds-Check-bypass-vulnerabilities.pdf
3mdeb points out that there is a patent by Intel with information focused on disabling Intel SMM.
Don’t click on this link if you’re an engineer and are not allowed to view patent information.
IA32-doc:: put as many definitions from the Intel Manual into machine-processable format (in this case: yaml) as possible.
https://github.com/wbenny/ia32-doc
Re: https://firmwaresecurity.com/2018/07/11/intel-releases-a-dozen-new-security-advisories/
at least one of these recent Intel bugs should also be in the Tianocore Security Advisories list, and at least one of them was just added to it:
https://legacy.gitbook.com/book/edk2-docs/security-advisory/details
eg:
Re: https://firmwaresecurity.com/2018/07/11/intel-releases-a-dozen-new-security-advisories/
In an effort to continuously improve the robustness of the Intel® Converged Security Management Engine (Intel® CSME), Intel has performed a security review of its Intel® CSME with the objective of continuously enhancing firmware resilience. As a result, Intel has identified security vulnerabilities that could potentially place affected platforms at risk.[…]
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00112.html
I’ve only seen them release 1 or 2 at a time, a dozen new advisories in a day is a LOT:
https://www.intel.com/content/www/us/en/security-center/default.html
Insecure Handling of BIOS and AMT Passwords
EDK II Untested memory not covered by SMM page protection
Platform firmware included insecure handling of certain UEFI variables
Intel® Quartus® Prime Pro
Firmware Authentication Bypass
Intel® Quartus Family of Tools Privilege Escalation Vulnerability
Insufficient Input Validation in Intel® VTune Amplifier, Intel® Advisor and Intel® Inspector products before version 2018 Update 3 potentially allows an unprivileged user to trigger a Denial of Service via local vector
BMC Firmware Vulnerability Intel Server Boards, Compute Modules and Systems
Insufficient Input Validation in Bleach module in Intel® Distribution for Python (IDP) version IDP 2018 Update 2 potentially allows an unprivileged user to bypass URI sanitization and cause a Denial of Service via local vector
Intel® Converged Security Management Engine (Intel® CSME) 11.x issue
Intel® Optane™ memory module update
Intel Q1’18 Intel® Active Management Technology 9.x/10.x/11.x Security Review Cumulative Update
Re: https://firmwaresecurity.com/2018/03/17/intel-publishes-pcie-device-security-enhancements-spec/
The PHY Interface for the PCI Express* (PIPE) Architecture Revision 5.1 is an updated version of the PIPE spec that supports PCI Express, SATA, USB, DisplayPort, and Converged I/O architectures.
The review draft PCI Express* Device Security Enhancements Specification Revision 0.7 defines PCIe* Device Firmware Measurement and PCIe* Device Authentication that enable a Host to query and verify the identity and capability of a PCIe* Device, to improve system security.
https://www.vusec.net/projects/tlbleed/
TLBleed is a new side channel attack that has been proven to work on Intel CPU’s with Hyperthreading (generally Simultaneous Multi-threading, or SMT, or HT on Intel) enabled. It relies on concurrent access to the TLB, and it being shared between threads. We find that the L1dtlb and the STLB (L2 TLB) is shared between threads on Intel CPU cores.
https://twitter.com/vpikhur/status/1016783086325940224
This appears to be a separate group than the Intel group that does the main security advisories. And for big stories, the main Intel PR team does announcements. This group appears to have 4 announcements so far. So there’s at least 3 places you have to check Intel for security updates now. 😦
https://01.org/security/advisories
https://01.org/security/advisories/intel-oss-10002
Intel Open Source Security Incident Response Team
Speculative Execution Branch Prediction Side Channel and Branch Prediction Analysis Method
Intel ID: INTEL-OSS-10002
Last revised: 07/10/2018
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00127.html
Existing UEFI setting restrictions for DCI (Direct Connect Interface) in 5th and 6th generation Intel® Xeon® Processor E3 Family, Intel® Xeon® Scalable processors, and Intel® Xeon® Processor D Family can potentially allow a limited physical presence attacker to access platform secrets via debug interfaces.
the PDF that was not previously available appears to be available…
https://blog.cyberus-technology.de/posts/2018-06-06-intel-lazyfp-vulnerability.html
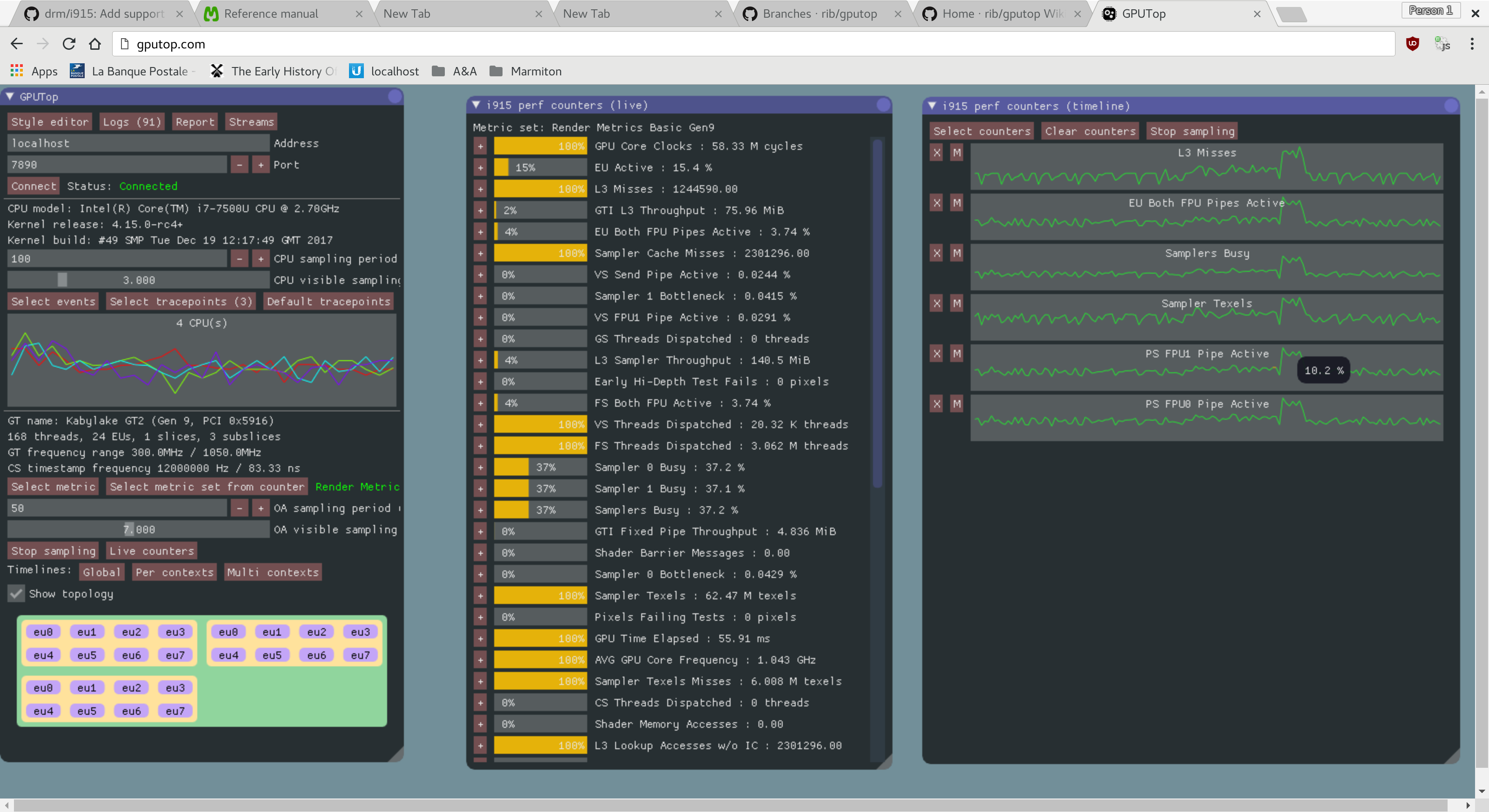
Intel posted info about a new blog post using GPUTop with Caledon (Intel-flavored Android):
We are excited to bring out a new tutorial for profiling gpu on Android. Gputop exposes many GPU parameters module wise such as frequency, busyness, threads, EU activeness etc. These are very helpful in identifying performance bottlenecks as well as impact of performance improvements on the GPU either through graphics software stack or through the graphics application. If you are learning/ new to gpu, this should attract you even more. Please take a look, try out and feel free to share your feedback.
https://01.org/projectceladon/documentation/tutorials/profiling-gpu
GPU Top is a tool to help developers understand GPU performance counters and provide graphical and machine readable data for the performance analysis of drivers and applications. GPU Top is compatible with all GPU programming apis such as OpenGL, OpenCL or Vulkan since it primarily deals with capturing periodic sampled metrics. GPU Top so far includes a web based interactive UI as well as a non-interactive CSV logging tool suited to being integrated into continuous regression testing systems. Both of these tools can capture metrics from a remote system so as to try an minimize their impact on the system being profiled. GPUs supported so far include: Haswell, Broadwell, Cherryview, Skylake, Broxton, Apollo Lake, Kabylake, Cannonlake and Coffeelake.
https://lists.01.org/mailman/listinfo/celadon
https://blog.benjojo.co.uk/post/interactive-x86-bootloader-tutorial
The tutorial ends with a pointer to some BIOS interrupts. It should have mentioned Ralph Brown’s classic list.
http://www.cs.cmu.edu/~ralf/files.html
https://en.wikipedia.org/wiki/Ralf_Brown%27s_Interrupt_List
Re: https://firmwaresecurity.com/2018/06/15/intel-security-conference/
More details are available:
iSecCon 2018: Intel Security Conference 2018
Intel Ronler Acres 4 (RA4), 2501 NW Century Blvd
Hillsboro, OR, United States, December 4-5, 2018
PROGRAM COMMITTEE:
* Rodrigo Branco (BSDaemon), Chief Security Researcher, Intel Corporation (STrategic Offensive Research & Mitigations – STORM, IPAS)
* Deepak K Gupta, Security Researcher, Intel Corporation (Windows OS Group)
* Marion Marschalek, Senior Security Researcher, Intel Corporation (STrategic Offensive Research & Mitigations – STORM, IPAS)
* Martin Dixon, Chief Security Architect, Intel Corporation (IPAS)
* Vincent Zimmer, Senior Principal Engineer, Intel Corporation (Software and Services Group)
* Matt Miller, Partner, Microsoft Corporation
* Cesar Cerrudo, CTO, IOActive
* Thomas Dullien (“Halvar Flake”), Staff Engineer, Google Project Zero
* Shay Gueron, Senior Principal Engineer, Amazon Web Services (AWS)
[…]Earlier this year, Julian Stecklina (Amazon) and Thomas Prescher (Cyberus Technology) jointly discovered and responsibly disclosed another vulnerability that might be part of these, and we call it LazyFP. LazyFP (CVE-2018-3665) is an attack targeting operating systems that use lazy FPU switching. This article describes what this attack means, outlines how it can be mitigated and how it actually works.
For further details, see the current draft of the lazyFP paper: <Link withheld by request from Intel>
Please check back regularly, we’re going to update this post in coordination with Intel.[…]
http://blog.cyberus-technology.de/posts/2018-06-06-intel-lazyfp-vulnerability.html
The above tweet is all I know so far. The URL in that link doesn’t appear to be useful (unless you’re one of the committee).
Please post more details.
Please host it in Seattle!!!! 🙂
Chip vendors controlling the security of OSes should be more transparent in their selection process. They should maintain a list of OSVs that they maintain embargoed fixes. Then uses could determine if they want to trust the OS or not, or try to lobby to try and get the ISA vendor to support their OS. Is the OS on the list, ok then they may have some chance at fixing things. If not on the list I expect to be vulnerable until the embargo ends. There are MANY more OSes than Microsoft Windows, Apple macOS, a limited number of Linux distros, and sometimes FreeBSD.
In some forums, Bryan Cantrill is crafting a fiction. He is saying the FPU problem (and other problems) were received as a leak. He is not being truthful, inventing a storyline, and has not asked me for the facts. This was discovered by guessing Intel made a mistake. We are doing the best for OpenBSD. Our commit is best effort for our user community when Intel didn’t reply to mails asking for us to be included. But we were not included, there was no reply. End of story. That leaves us to figure things out ourselves. Bryan is just upset we guessed right. It is called science.
https://marc.info/?l=openbsd-tech&m=152894815409098&w=2
June 14, 2018
The vulnerability allowed exploiting a critical flaw in Intel Management Engine and still can be present in equipment of vendors that use Intel processors. Apple released an update for macOS High Sierra 10.13.4, which fixes the firmware vulnerability CVE-2018-4251 found by Positive Technologies experts Maxim Goryachy and Mark Ermolov. For more details, see Apple Support.[…]
http://blog.ptsecurity.com/2018/06/apple-fixed-vulnerability-founde-by-PT-experts.html
http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2018-4251
https://support.apple.com/en-us/HT208849
Here’s the source of the Intel floating point issue:
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00145.html
Re: https://firmwaresecurity.com/2018/06/13/intel-floating-point-issue/
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Discover the Desktop
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
News from coreboot world
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Just another WordPress.com site
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
You must be logged in to post a comment.