Wow, amazing!
Inside a low budget consumer hardware espionage implant
Analysis of the S8 data line locator
mich @0x6d696368
The following analysis was performed on a S8 data line locator […]A while back Joe Fitz tweeted about the S8 data line locator1. He referred to it as “Trickle down espionage” due to its reminiscence of NSA spying equipment. The S8 data line locator is a GSM listening and location device hidden inside the plug of a standard USB data/charging cable. It supports the 850, 900, 1800 and 1900 MHz GSM frequencies. Its core idea is very similar to the COTTONMOUTH product line by the NSA/CSS [1] in which an RF device is hidden inside a USB plug. Those hidden devices are referred to as implants. The device itself is marketed as a location tracker usable in cars, where a thief would not be able to identify the USB cable as a location tracking device. Its malicious use-cases can, however, not be denied. Especially since it features no GPS making its location reporting very coarse (1.57 km deviation in my tests). It can, e.g., be called to listen to a live audio feed from a small microphone within the device, as well as programmed to call back if the sound level surpasses a 45 dB threshold. The fact that the device can be repackaged in its sliding case, after configuring it, i.e. inserting a SIM, without any noticeable marks to the packaging suggests its use-case: covert espionage.[…]
I was not able yet to write new firmware via flashrom because I was not able to disable block protection on the flash, yet. Maybe a different avenue for flashing new firmware could be the SPFlash tool4 and/or the Flash tool. However, that would not be open source. If know something about the weird FAT12 file system used in the device or are able to flash your S8 data line locator please contact me with details![…]
No writeup would be complete without at least one fuck up. So here it is: While using the S8 data line locator with OpenBTS I provisioned imaginary numbers. When switching SIM cards I forgot to turn of the voice activated callback. So long story short, some guy with the number 3333333 listend in on me for 2 minutes:
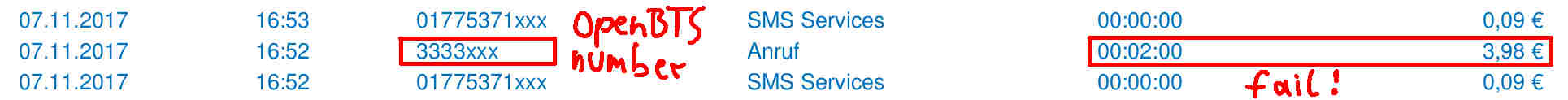 Provider call log fail. I did not notice this until I reviewed the logs! So my resume on these little hardware espionage implants: They are stealthy and dangerous as fuck![…]
Provider call log fail. I did not notice this until I reviewed the logs! So my resume on these little hardware espionage implants: They are stealthy and dangerous as fuck![…]



You must be logged in to post a comment.