https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00289.html
https://github.com/KitMurdock/plundervolt

Modern CPU architectures offer strong isolation guarantees towards user applications in the form of enclaves. For instance, Intel’s threat model for SGX assumes fully trusted enclaves, yet there is an ongoing debate on whether this threat model is realistic. In particular, it is unclear to what extent enclave malware could harm a system. In this work, we practically demonstrate the first enclave malware which fully and stealthily impersonates its host application. Together with poorly-deployed application isolation on personal computers, such malware can not only steal or encrypt documents for extortion, but also act on the user’s behalf, e.g., sending phishing emails or mounting denial-of-service attacks. Our SGX-ROP attack uses new TSX-based memory-disclosure primitive and a write-anything-anywhere primitive to construct a code-reuse attack from within an enclave which is then inadvertently executed by the host application. With SGX-ROP, we bypass ASLR, stack canaries, and address sanitizer. We demonstrate that instead of protecting users from harm, SGX currently poses a security threat, facilitating so-called super-malware with ready-to-hit exploits. With our results, we seek to demystify the enclave malware threat and lay solid ground for future research on and defense against enclave malware.
(Submitted on 8 Oct 2018)
Intel has introduced a trusted computing technology, Intel Software Guard Extension (SGX), which provides an isolated and secure execution environment called enclave for a user program without trusting any privilege software (e.g., an operating system or a hypervisor) or firmware. Nevertheless, SGX is vulnerable to several side channel attacks (e.g. page-fault-based attack and cache-based attack). In this paper, we explore a new, yet critical side channel attack in SGX, interface-based side channel attack, which can infer the information of the enclave input data. The root cause of the interface-based side channel attack is the input dependent interface invocation information (e.g., interface information and invocation patterns) which can be observed by the untrusted privilege software can reveal the control flow in the enclave. We study the methodology which can be used to conduct the interface-based side channel attack. To illustrate the effectiveness of the interface-based side-channel attacks, we use our methodology to infer whether tracked web pages have been processed by the SGX-assisted NFV platforms and achieve the accuracy of 87.6% and recall of 76.6%. We also identify the packets which belong to the tracked web pages, with the accuracy of 67.9%and recall of 71.1%. We finally propose some countermeasures to defense the interface-based side channel attack in SGX-assisted applications.
Intel has a new document about hardware security and SGX:
There is tremendous opportunity for application and solution developers to take charge of their data security using new hardware-based controls for cloud and enterprise environments. Intel® Software Guard Extensions (Intel® SGX), available in its second-generation on the new Intel® Xeon® E-2100 processor, offers hardware-based memory encryption that isolates specific application code and data in memory. Intel® SGX allows user-level code to allocate private regions of memory, called enclaves, which are designed to be protected from processes running at higher privilege levels. We believe only Intel offers such a granular level of control and protection. Think about it like a lockbox in your home. Even though you have locks on your doors and a home security system, you may still secure your most sensitive data in a private lockbox with a separate key to provide extra layers of protection even if someone gained unwanted access to your home. Essentially, Intel® SGX is a lockbox inside a system’s memory, helping protect the data while it’s in-use during runtime.[…]
Reflections on trusting SGX
by Mark Silberstein
Sep 25, 2018
The security community will remember the year of 2018 as the year of speculative execution attacks. Meltdown and Spectre, the recent Foreshadow (L1TF in Intel’s terminology), and their variants demonstrate how the immense processor design complexity, perpetual drive for higher performance, and subtle hardware-software interactions — all collude to create a major system security earthquake that is shaking the whole industry. Foreshadow stands out in that it wreaks havoc on Intel SGX, Intel’s recent instruction set extension for building trusted execution environments, which has been envisioned as a stronghold of security in future computing systems. In this blog I highlight the important differences between Foreshadow and other speculative execution attacks, and raise a few questions that require much more than just a technical solution.[…]
An Intel response to a question about SGX support on Celadon (Intel’s flavor of Android, tuned for Intel systems):
“By now there is no plan to support SGX for Android. Hope it clarifies.”
https://lists.01.org/pipermail/celadon/2018-August/001280.html
Security researchers have identified a speculative execution side-channel method called L1 Terminal Fault (L1TF). This method impacts select microprocessor products supporting Intel® Software Guard Extensions (Intel® SGX). Further investigation by Intel has identified two related applications of L1TF with the potential to impact additional microprocessors, operating systems, system management mode, and virtualization software. If used for malicious purposes, this class of vulnerability has the potential to improperly infer data values from multiple types of computing devices.[…]
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00161.html
https://www.intel.com/content/www/us/en/architecture-and-technology/l1tf.html
https://access.redhat.com/security/vulnerabilities/L1TF
https://www.redhat.com/en/blog/understanding-l1-terminal-fault-aka-foreshadow-what-you-need-know
https://blogs.technet.microsoft.com/virtualization/2018/08/14/hyper-v-hyperclear/
https://www.us-cert.gov/ncas/current-activity/2018/08/14/Intel-Side-Channel-Vulnerability
This blog-post provides the reader with an overview of the Intel SGX technology. In this first part, we explore the additions made to Intel platforms to support SGX, focusing on the processor and memory. We then explain the management and life cycle of an enclave. Finally, we detail two features of enclaves: secret sealing and attestation.[…]
https://blog.quarkslab.com/overview-of-intel-sgx-part-1-sgx-internals.html
https://github.com/chipsec/chipsec/commit/45b50782c9585f79e1f01d5262ad0022f78540a5
Module name: ‘sgx_check’
Author: Sushmith Hiremath, INTEL DCG RED team
Check SGX related configuration
Reference: SGX BWG, CDI/IBP#: 565432
I’m unclear to the meaning of the numeric Reference #…
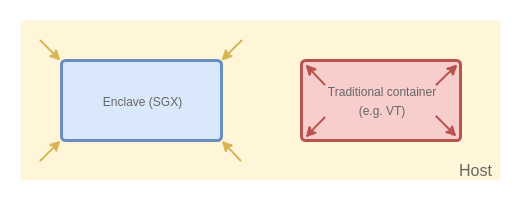
Jun 11, 2018 by Joanna Rutkowska
A few months ago, during my keynote at Black Hat Europe, I was discussing how we should be limiting the amount of trust when building computer systems. Recently, a new technology from Intel has been gaining popularity among both developers and researchers, a technology which promises a big step towards such trust-minimizing systems. I’m talking about Intel SGX, of course. Intel SGX caught my attention for the first time about 5 years ago, a little while before Intel has officially added information about it to the official Software Developer’s Manual. I’ve written two posts about my thoughts on this (then-upcoming) technology, which were a superposition of both positive and negative feelings. Over the last 2 years or so, together with my team at ITL, we’ve been investigating this fascinating technology a bit closer. Today I’d like to share some introductory information on this interesting project we’ve been working on together with our friends at Golem for several months now.[…]
https://blog.invisiblethings.org/2018/06/11/graphene-ng.html
Lots of news are filled with news about the latest version of CHIPSEC released. I don’t see that, but there are some interesting new checkins w/r/t ACPI support:
ACPI_TABLE_SIG_BGRT = ‘BGRT’
ACPI_TABLE_SIG_LPIT = ‘LPIT’
ACPI_TABLE_SIG_ASPT = ‘ASPT’
+ACPI_TABLE_SIG_FIDT = ‘FIDT’
+ACPI_TABLE_SIG_HEST = ‘HEST’
+ACPI_TABLE_SIG_BERT = ‘BERT’
+ACPI_TABLE_SIG_ERST = ‘ERST’
+ACPI_TABLE_SIG_EINJ = ‘EINJ’
+ACPI_TABLE_SIG_TPM2 = ‘TPM2’
+ACPI_TABLE_SIG_WSMT = ‘WSMT’
+ACPI_TABLE_SIG_DBG2 = ‘DBG2’
+ACPI_TABLE_SIG_NHLT = ‘NHLT’
+ACPI_TABLE_SIG_MSCT = ‘MSCT’
+ACPI_TABLE_SIG_RASF = ‘RASF’
+ACPI_TABLE_SIG_SPMI = ‘SPMI’
+ACPI_TABLE_SIG_OEM1 = ‘OEM1’
+ACPI_TABLE_SIG_OEM2 = ‘OEM2’
+ACPI_TABLE_SIG_OEM3 = ‘OEM3’
+ACPI_TABLE_SIG_OEM4 = ‘OEM4’
+ACPI_TABLE_SIG_NFIT = ‘NFIT’
as well as some new SGX support… Fun!
https://twitter.com/qrs/status/992109956659863552
[…]Today we’re excited to announce Asylo (Greek for “safe place”), a new open-source framework that makes it easier to protect the confidentiality and integrity of applications and data in a confidential computing environment. Asylo is an open-source framework and SDK for developing applications that run in trusted execution environments (TEEs). TEEs help defend against attacks targeting underlying layers of the stack, including the operating system, hypervisor, drivers, and firmware, by providing specialized execution environments known as “enclaves”. TEEs can also help mitigate the risk of being compromised by a malicious insider or an unauthorized third-party. Asylo includes features and services for encrypting sensitive communications and verifying the integrity of code running in enclaves, which help protect data and applications.[…]
https://twitter.com/vpikhur/status/989561250609709057
PATENT ALERT. Engineers not wanting to be tainted by external patent info should not read this post. It is only the title/abstract of the patent, however.
.
.
.
.
.
.
.
Inventor: Volodymyr Pikhur, Atul A. Khare
Current Assignee: Intel Corp
Priority date: 2016-09-07
Non-enclave access prevention
A processing system includes an execution unit comprising a logic circuit to implement an architecturally-protected execution environment associated with a protected region in a memory, in which the execution unit is to execute application code stored in the protected region as a thread running in the architecturally-protected execution environment, determine that an access mode flag is set to a first value, detect an attempt by the thread to access data stored outside the protected region, and responsive to detecting the attempt and determining that the access mode flag is set to the first value, generate an exception.
Intel® SGX SDK Edger8r and Intel® Software Guard Extensions Platform Software Component
Intel ID: INTEL-SA-00117
Product family: Intel® SGX
Impact of vulnerability: Elevation of Privilege
Severity rating: Important
Original release: Mar 19, 2018
[…]CVE-2018-3626: The Edger8r tool in the Intel® Software Guard Extensions (SGX) Software Development Kit (SDK) before version 2.1.2 (Linux) and 1.9.6 (Windows) may generate code that is susceptible to a side channel attack, potentially allowing a local user to access unauthorized information. CVE-2018-5736: An elevation of privilege in Intel® Software Guard Extensions Platform Software Component before 1.9.105.42329 allows a local attacker to execute arbitrary code as administrator. CVE-2018-3626: Recently it was reported that the Edger8r Tool, a software component of the Intel® Software Guard Extensions (SGX) Software Development Kit (SDK), may generate C source code potentially leading to a software based side-channel vulnerability. […]Intel would like to thank Jo Van Bulck, Frank Piessens, and Raoul Strackx of Ku Leuven University for reporting CVE-2018-3626 and working with us on coordinated disclosure.
https://security-center.intel.com/advisory.aspx?intelid=INTEL-SA-00117&languageid=en-fr
A cureted list of system papers using/about Intel SGX. I’ll try to keep this list updated. I gladly accept PRs.
https://github.com/vschiavoni/sgx-papers
SgxPectre Attacks: Leaking Enclave Secrets via Speculative Execution
Guoxing Chen, Sanchuan Chen, Yuan Xiao, Yinqian Zhang, Zhiqiang Lin, Ten H. Lai
(Submitted on 25 Feb 2018)
This paper presents SgxPectre Attacks that exploit the recently disclosed CPU bugs to subvert the confidentiality of SGX enclaves. Particularly, we show that when branch prediction of the enclave code can be influenced by programs outside the enclave, the control flow of the enclave program can be temporarily altered to execute instructions that lead to observable cache-state changes. An adversary observing such changes can learn secrets inside the enclave memory or its internal registers, thus completely defeating the confidentiality guarantee offered by SGX. To demonstrate the practicality of our SgxPectre Attacks, we have systematically explored the possible attack vectors of branch target injection, approaches to win the race condition during enclave’s speculative execution, and techniques to automatically search for code patterns required for launching the attacks. Our study suggests that any enclave program could be vulnerable to SgxPectre Attacks since the desired code patterns are available in most SGX runtimes (e.g., Intel SGX SDK, Rust-SGX, and Graphene-SGX).
https://arxiv.org/abs/1802.09085
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Consolidated SNIA Blog
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Discover the Desktop
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
News from coreboot world
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Just another WordPress.com site
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
You must be logged in to post a comment.