[[Update: adding Tweet with announcement:
]]
This new plugin looks powerful!
Contributors:
Alex Matrosov (@matrosov)
Andrey Labunets (@isciurus)
Philip Lebedev (@p41l)
Yegor Vasilenko (@yeggor)
https://github.com/binarly-io/efiXplorer

[[Update: adding Tweet with announcement:
]]
This new plugin looks powerful!
Contributors:
Alex Matrosov (@matrosov)
Andrey Labunets (@isciurus)
Philip Lebedev (@p41l)
Yegor Vasilenko (@yeggor)
https://github.com/binarly-io/efiXplorer

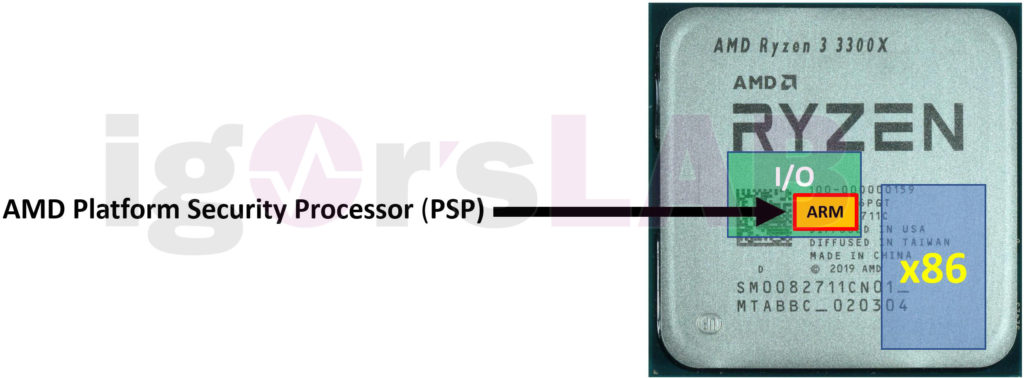
AMD UEFI Inside: What is really behind AGESA, the PSP (Platform Security Processor) and especially Combo PI?
Igor Wallossek
Since there are always questions and some things are often confused, we will give you some insights into AMD-UEFI, what is colloquially called “the BIOS” (although it is no longer correct). I have also broken down the following extremely to remain as simple and understandable as possible. Nevertheless, what happens when the PC starts up is the classic hen-and-egg problem that you simply have to talk about. Software starts hardware, whereas hardware without software does not actually work and software without hardware does nothing. Now what?[…]
In BOTH English and German:
HelloAmdHvPkg is a type-1 research hypervisor for AMD processors. The hope is to help researchers learn implementation required for the operating system start up under AMD-V (SVM: Secure Virtual Machine).[…]
https://github.com/tandasat/HelloAmdHvPkg
ACPICA and dmicheck updated. Multiple changes to multiple ACPI table checks. New Dmicheck testing. See announcement for long list of features and bugfixes.
http://fwts.ubuntu.com/release/fwts-V20.06.01.tar.gz
https://wiki.ubuntu.com/FirmwareTestSuite/ReleaseNotes/20.06.01
https://lists.ubuntu.com/mailman/listinfo/fwts-announce
https://launchpad.net/~firmware-testing-team/+archive/ubuntu/ppa-fwts-stable
see this Comment on that post:
This is the original codebase:
This is a small utility which checks and recomputes sha1 hashes used to validate Lenovo ThinkPad X220/T420 (and probably other Sandy Bridge ThinkPads) firmware integrity. You can hear 5 beeps twice if the firmware fails validation and you have TPM (security chip) turned on, which is pretty common for modified firmwares.[…]
https://github.com/ValdikSS/thinkpad-shahash/
But the one in the previous blog post has had a recent checkin, whereas this one has had no changes in a long time, so the new branch still may be of interest. Change is in this file:
Not to be confused with the Capstone Engine: the ECE Capstone Project: a current project at Oregon State University:
Our goal is to develop a software tool that when supplied with images of a printed circuit board will reverse engineer the netlist for the board. The software will be implemented as a web based service allowing for users to publish the netlist that they generate. This web page will be available to the engineering community for prolonging the life of old equipment as well as documenting systems for repair to reduce waste. Integrating Computer Vision & Deep Learning to the software, this project is aimed to provide precision and reliability without compromises.[…]
https://sites.google.com/oregonstate.edu/ece44x201913/completion-timeline
https://eecs.oregonstate.edu/project-showcase/projects/?id=DjjEhrfP6Jv0yWqi
So far, the only info are these tweets:
Microsoft Defender has been a Windows-cenric AV tool. Recently, Microsoft has ported it to Android and Linux. Recently, Microsoft also started adding UEFI scanning to Defender. So maybe now Android and Linux users can use Defender to scan for UEFI vulns?
CHIPSEC has been the main option for UEFI scanning. It works only on Intel systems. It works as an OS-level app (“OS-present”) on Mac, Windows, and Linux. And runs on UEFI. The OS-level scanners from Apple and Microsoft now both cover UEFI. Will either scan non-Intel systems: ARM64 and AMD64?
AMD issued an update last week saying that it will provide an actual update in a few weeks, and sarcastically advises vendors to stay “up-to-date”…
6/17/20
AMD is aware of new research related to a potential vulnerability in AMD software technology supplied to motherboard manufacturers for use in their Unified Extensible Firmware Interface (UEFI) infrastructure and plans to complete delivery of updated versions designed to mitigate the issue by the end of June 2020.[…]AMD has delivered the majority of the updated versions of AGESA to our motherboard partners and plans to deliver the remaining versions by the end of June 2020. AMD recommends following the security best practice of keeping devices up-to-date with the latest patches.[…]
We thank Danny Odler for his ongoing security research.
Full announcement paragraph:
https://www.amd.com/en/corporate/product-security
No news here:
https://developer.arm.com/support/arm-security-updates
AGESA status page:
just kidding, there is no such page, only AMD clients get AGESA status updates under NDA.
I wonder if the Apple macOS or Microsoft Defender UEFI scanners will be updated to catch this on AMD systems. CHIPSEC can’t, it does not work on AMD systems.
[The main branch is 9 months old, but there’s another branch that has just been updated…]
Tools to check and cryptographically sign UEFI firmware images found in ThinkPads. This will resolve the issue where your ThinkPad lets out two groups of five beeps before continuing to boot (the error indicating an invalid signature). These tools are written in Python 3 and rely on the “pycryptodome” library.[…]
By: Nidhi Rastogi, Sharmishtha Dutta, Mohammed J. Zaki, Alex Gittens, Charu Aggarwal
Malware threat intelligence uncovers deep information about malware, threat actors, and their tactics, Indicators of Compromise(IoC), and vulnerabilities in different platforms from scattered threat sources. This collective information can guide decision making in cyber defense applications utilized by security operation centers(SoCs). In this paper, we introduce an open-source malware ontology – MALOnt that allows the structured extraction of information and knowledge graph generation, especially for threat intelligence. The knowledge graph that uses MALOnt is instantiated from a corpus comprising hundreds of annotated malware threat reports. The knowledge graph enables the analysis, detection, classification, and attribution of cyber threats caused by malware. We also demonstrate the annotation process using MALOnt on exemplar threat intelligence reports. A work in progress, this research is part of a larger effort towards auto-generation of knowledge graphs (KGs)for gathering malware threat intelligence from heterogeneous online resources.
https://github.com/shoron-dutta/MALOnt
https://arxiv.org/abs/2006.11446
Firmware Command and Control will create an agile embedded response capability foundational with baselined firmware and behaviors with bi-directional sharing of threat to upstream energy security operations
Value Proposition
* Embedded devices control the most critical functions on the electric grid with little to no insight into the firmware or ability to mitigate from cyber attacks.
* The adversaries have ‘raced to the bottom’ hiding access in embedded devices
* Firmware will be baselined to detect changes with advanced ML similarity with constraints
* Embedded host agile response
* Structured threat sharing between the device and upstream security
* Firmware C2 will monitor and mitigate previously unmonitored devices controlling the most critical functions in the electric grid.
Project Objectives:
* Baselined embedded firmware with all constraints for setting changes
* Low-impact cyber operations protected/hidden from adversaries
* Structured Threat: Visual, Sharable, Actionable, and Implementable (IT/OT)
* Firmware C2 uses recent ML concepts to baseline firmware to detect unexplained changes, described in structured threat for bi-direction upstream energy security operations actions and awareness.
FirmWare Test Suite’s ACPI tests are improving. It sounds like they are acpica-dump compatible now, and FTWS dumps more than acpidump!
[PATCH 1/2] doc: add new –dump-acpi-from-sysfs option
https://lists.ubuntu.com/archives/fwts-devel/2020-June/012068.html
[PATCH 0/2] make the acpi logs from fwts can be used acpica debugging
https://lists.ubuntu.com/archives/fwts-devel/2020-June/012013.html
“-dumpfile=acpidump.log: load ACPI tables from output generated from acpidump or from sudo fwts –dump. The latter is preferred as fwts –dump is able to dump more tables than acpidump.[…]
SymCC is a compiler wrapper which embeds symbolic execution into the program during compilation, and an associated run-time support library. In essence, the compiler inserts code that computes symbolic expressions for each value in the program. The actual computation happens through calls to the support library at run time. To build the pass and the support library, make sure that LLVM 8, 9 or 10 and Z3 version 4.5 or later, as well as a C++ compiler with support for C++17 are installed. […]
https://github.com/eurecom-s3/symcc
http://www.s3.eurecom.fr/tools/symbolic_execution/symcc.html
https://github.com/danielmgmi/IntelMCDowngrade
IntelMCDowngrade: Scripts to collect microcode from CPUMicrocodes Repo and to downgrade to a compatible microcode.[…]
Samsung AArch64-centric:
In previous posts, we explained how to dump Exynos bootROM and reverse its USB stack.[…]
https://fredericb.info/2020/06/exynos-usbdl-unsigned-code-loader-for-exynos-bootrom.html
NetBSD’s UEFI bootloader is getting some new features; Module support should get interesting.
http://mail-index.netbsd.org/source-changes/2020/06/21/msg118558.html
http://mail-index.netbsd.org/source-changes/2020/06/21/msg118549.html
Hmm, it seems that Alex Ionescu, author of VisualUEFI has disappeared online, partially.
I was going to point someone to an old post of his on Windows binaries included in WBPT ACPI, for an answer to the below question:
but it appears his Twitter account is no longer active and all the old tweets are gone:
His web site appears to be blank (default, unconfigured) state:
The Github web page for Alex has a link to his Twitter URL, which appears to redirect to another user:
https://github.com/aionescu (maybe this is innocent Github redirection foo?).
Just being a bit paranoid, but maybe you should be careful about using some of the binaries checked into VisualUEFI:
https://github.com/ionescu007/VisualUefi
Keep an eye out for any strange checkins:
https://github.com/ionescu007/VisualUefi/commits/master
I’ve probably missed something and he’s moved onto another account or something. But be careful with anything in binary (or source form) online, in general, anyway.
If someone can clarify things, please leave a Comment on this post. Thanks.
This utility is an app indicator (tray icon) to help you reboot into other OSes, or UEFI/BIOS, or the same OS. Instead of picking the OS you want during reboot at the grub menu, you can just preselect it from the menu here. Basically it’s a wrapper around grub-reboot. I’ve only tested this on Ubuntu 20.04.
https://github.com/mendhak/grub-reboot-picker

[ This is 2 year old news, but I’m just learning about it… 😦 ]
Wireshark is a tool used to sniff network packets and dissect the protocols and help debug them. Since version 3.0.0 or so, you can use Wireshark to sniff TPM v2. Not the hardware TPM chip, but a TPM2 simulator, which is simulated over the network, so Wireshark can capture it, and there’s a Wireshark Dissector (parser) for TPM2 protocol.
https://www.wireshark.org/lists/wireshark-commits/201804/msg00451.html
Documentation:
https://www.wireshark.org/docs/dfref/t/tpm.html
Sample PCAP:
https://wiki.wireshark.org/SampleCaptures?action=AttachFile&do=get&target=policy-authorizeNV.pcap
Created by the TPM2 community:
https://github.com/tpm2-software
There is a brief mention of this Wireshark TPM2 dissector in this FOSDEM presentation:
PS: Mostly only related by the “Shark” suffix string, but if you are debugging Linux, KernelShark is a nice tool. I haven’t tried it with a TPM, but you might be able to see Linux kernel TPM trace log traffic through KernelShark…
https://kernelshark.org/
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Discover the Desktop
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
News from coreboot world
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
Just another WordPress.com site
Hastily-written news/info on the firmware security/development communities, sorry for the typos.
You must be logged in to post a comment.